| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | ||
| 6 | 7 | 8 | 9 | 10 | 11 | 12 |
| 13 | 14 | 15 | 16 | 17 | 18 | 19 |
| 20 | 21 | 22 | 23 | 24 | 25 | 26 |
| 27 | 28 | 29 | 30 |
- 디지털포렌식
- 25 Days of Cyber Security
- 포렌식
- INFOSEC
- 리눅스마스터 자격증
- kali-linux
- 리눅스마스터 2급 2차
- 해킹
- 정보보안산업기사 자격증
- 디지털포렌식 전문가 2급
- 자격증
- TryHackeMe
- picoGym
- Capture The Flag
- hackthebox
- THM
- hacker
- 디지털포렌식 자격증
- CTF
- TryHackMe
- Cybersecurity
- Hack The Box
- Whitehacker
- flag
- 정보보안
- htb
- root
- picoCTF
- picoCTF 2021
- 정보보안산업기사 필기
- Today
- Total
root@j4sper:~#
25 Days of Cyber Security | Day 3 본문
| Workstation | |
| Virtual Box | VMware Fusion 12.1.1 |
| OS | kali-linux-2021.1 |
[Day 3] Christmas Chaos
McSkidy is walking down the corridor and hears a faint bleeping noise, Beep.... Beep.... Beep... as McSkidy gets closer to Sleigh Engineering Room the faint noise gets louder and louder.. BEEP.... BEEP.... Something is clearly wrong! McSkidy runs to the room, slamming open the door to see Santa's sleighs control panel lite up in red error messages! "Santa sleigh! It's been hacked, code red.. code red!" he screams as he runs back to the elf security command center.
Can you help McSkidy and his team hack into Santa's Sleigh to re-gain control?
Learning Objectives
- Understanding Authentication
- Understand the use of default credentials and why they're dangerous
- Bypass a login form using BurpSuite
Authentication
Authentication is a process of verifying a users' identity, normally by credentials (such as a username, user id or password); to put simply, authentication involves checking that somebody really is who they claim to be. Authorization (which is fundamentally different to authentication, but often used interchangeably) determines what a user can and can't access; authorization is covered in tomorrow walkthrough, today's task focuses on authentication and some common flaws.
Default Credentials
You've probably purchased (or downloaded a service/program) that provides you with a set of credentials at the start and requires you to change the password after it's set up (usually these credentials that are provided at the start are the same for every device/every copy of the software). The trouble with this is that if it's not changed, an attacker can look up (or even guess) the credentials.
What's even worse is that these devices are often exposed to the internet, potentially allowing anyone to access and control it. In 2018 it was reported that a botnet (a number of internet-connected devices controlled by an attacker to typically perform DDoS attacks) called Mirai took advantage of Internet of Things (IoT) devices by remotely logging, configuring the device to perform malicious attacks at the control of the attackers; the Mirai botnet infected over 600,000 IoT devices mostly by scanning the internet and using default credentials to gain access.
In fact, companies such as Starbucks and the US Department of Defense have been victim to leaving services running with default credentials, and bug hunters have been rewarded for reporting these very simple issues responsibly (Starbucks paid $250 for the reported issue):
- https://hackerone.com/reports/195163 - Starbucks, bug bounty for default credentials.
- https://hackerone.com/reports/804548 - US Dept Of Defense, admin access via default credentials.
In 2017, it was reported that 15% of all IoT devices still use default passwords.
SecLists is a collection of common lists including usernames, passwords, URLs and much more. A password list known as "rockyou.txt" is commonly used in security challenges, and should definitely be a part of your security toolkit.
Dictionary Attacks using BurpSuite
A dictionary attack is a method of breaking into an authenticated system by iterating through a list of credentials. If you have a list of default (or the most common) usernames and passwords, you can loop through each of them in hopes that one of the combinations is successful.
You can use a number of tools to perform a dictionary attack, one notable one being Hydra (a fast network logon cracker) and BurpSuite, an industry-standard tool used for web application penetration testing. Given day 3 is about web exploitation, we'll show you how to use BurpSuite to perform a dictionary attack on a web login form.
To download BurpSuite click here, otherwise, BurpSuite is pre-installed on our web-based AttackBox.
- Start BurpSuite, you can do this on the AttackBox by clicking BurpSuite logo in the icon tray.

- Once this has loaded, you want to "Intercept" your traffic by proxying it through the BurpSuite, which will then forward the request to the intended destination (in our case it will be a website) This will give you the ability to analyse and modify your browsers traffic.
- This example uses the AttackBox, and makes proxying traffic to BurpSuite easy (if you're using BurpSuite on your own machine, click here) to see how to proxy traffic to BurpSuite). On the AttackBox, open Firefox, click on the FoxyProxy browser extension, and select "Burp" - this will now proxy your traffic to BurpSuite.
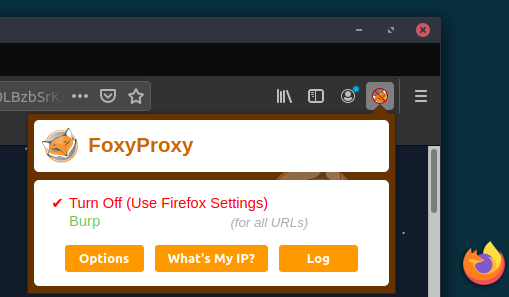
- Go to the BurpSuite application and click the Proxy tab, then click the button "Intercept is on".
- This example uses the AttackBox, and makes proxying traffic to BurpSuite easy (if you're using BurpSuite on your own machine, click here) to see how to proxy traffic to BurpSuite). On the AttackBox, open Firefox, click on the FoxyProxy browser extension, and select "Burp" - this will now proxy your traffic to BurpSuite.
- Navigate to your chosen website, as you're intercepting your traffic, you will see BurpSuite has held your request and will not forward it on until you tell it to. Let's go to our web application and submit your details into a given form, in our case its a generic login form.
- This captured request will show up in the Proxy tab. Right-click it, and click "Send to Intruder"; BurpSuite has a lot of functionality to repeat modify and manipulate requests, Burp Intruder is a tool to automate customize web attacks. We will use intruder to loop through and submit a login request using a list of default credential, in the hopes that one of the usernames and passwords in the list is correct.

- Go to the Intruder tab, you should see your request. Here we will insert "positions" (telling Burp which fields to update when automating a request), select a list per position and start the attack.
- Click the "Positions" tab, and clear the pre-selected positions.
- Add the username and password values as positions (highlight the text and click "Add")
- Select "Cluster Bomb" in the Attack type dropdown menu; this attack type iterates through each payloads sets in turn, so every combination of each set is tested.
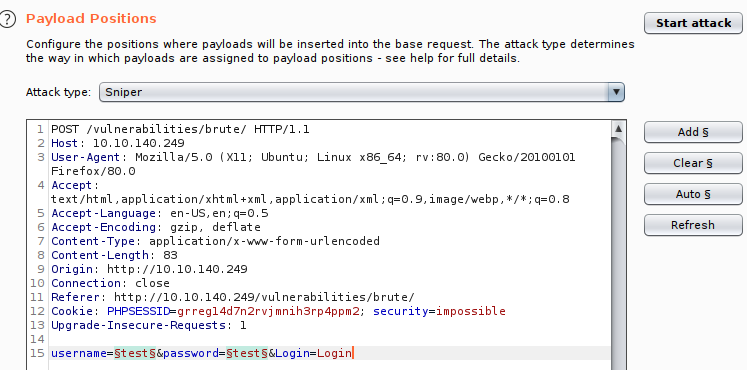
- We're going to tell each "Position" which Payload to use. In our example, we will select a list of usernames for the username field and a list of passwords for the password field.
- Click the "Payloads" tab, select your Payload set (set 1 is the username field, set 2 is the password field) and add select your list in the "Payload Options" section (or manually add entries).
- For set 1 (username), we will add a few common default username entries such as "admin", "root" and "user"

- For set 2 (password), we will add a few common default passwords such as "password", "admin" and "12345"
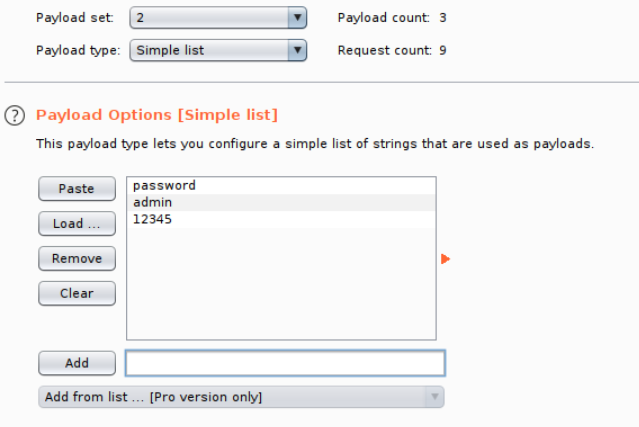
- Click the "Start Attack" button, this will loop through each position list in every combination. You can sort by the "Length" or "Status" to identify a successful login (typically all incorrect logins will have the same status or length, if a combination is correct it will be different.
Use what you've learnt to help McSkidy hack back into the Santa Sleigh Tracker!
start AttackBox

Deploy your AttackBox (the blue "Start AttackBox" button) and the tasks machine (green button on this task) if you haven't already. Once both have deployed, open Firefox on the AttackBox and copy/paste the machines IP (MACHINE_IP) into the browser search bar.

Use BurpSuite to brute force the login form. Use the following lists for the default credentials:
Username Password
root root
admin password
user 12345
Use the correct credentials to log in to the Santa Sleigh Tracker app. Don't forget to turn off Foxyproxy once BurpSuite has finished the attack!
Use BurpSuite
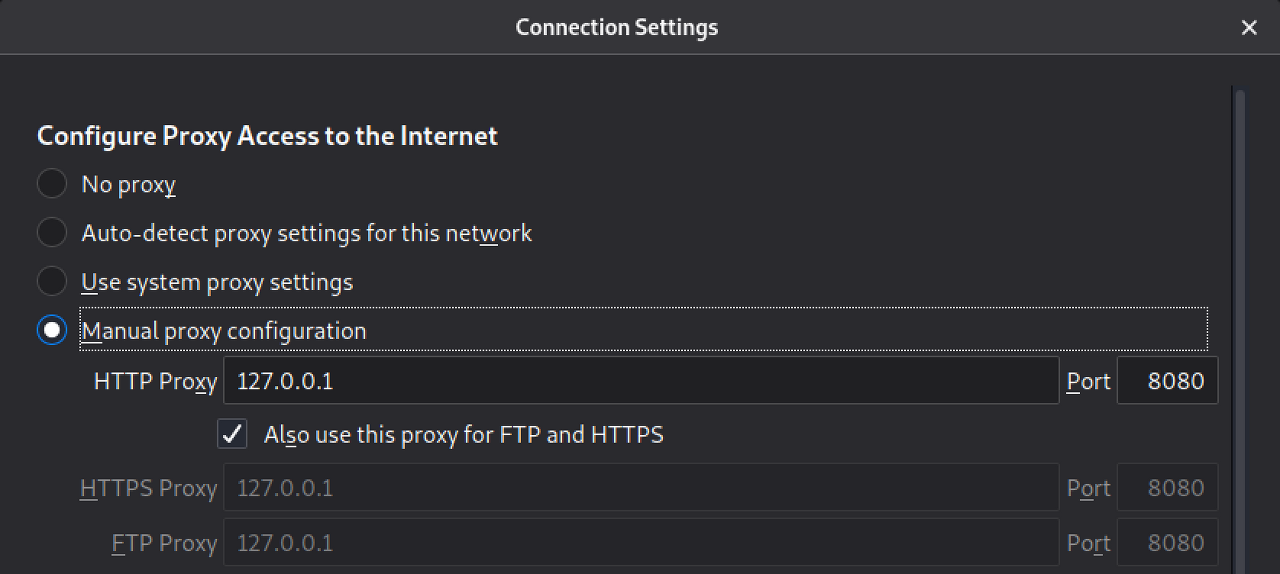
$ burpsuiteSet proxy set proxy in firefox browser
Menu bar → Preferences → Network Settings → Manual proxy configuration
Login admin admin, Send to Intruder

Select Cluster bomb

Set Payload
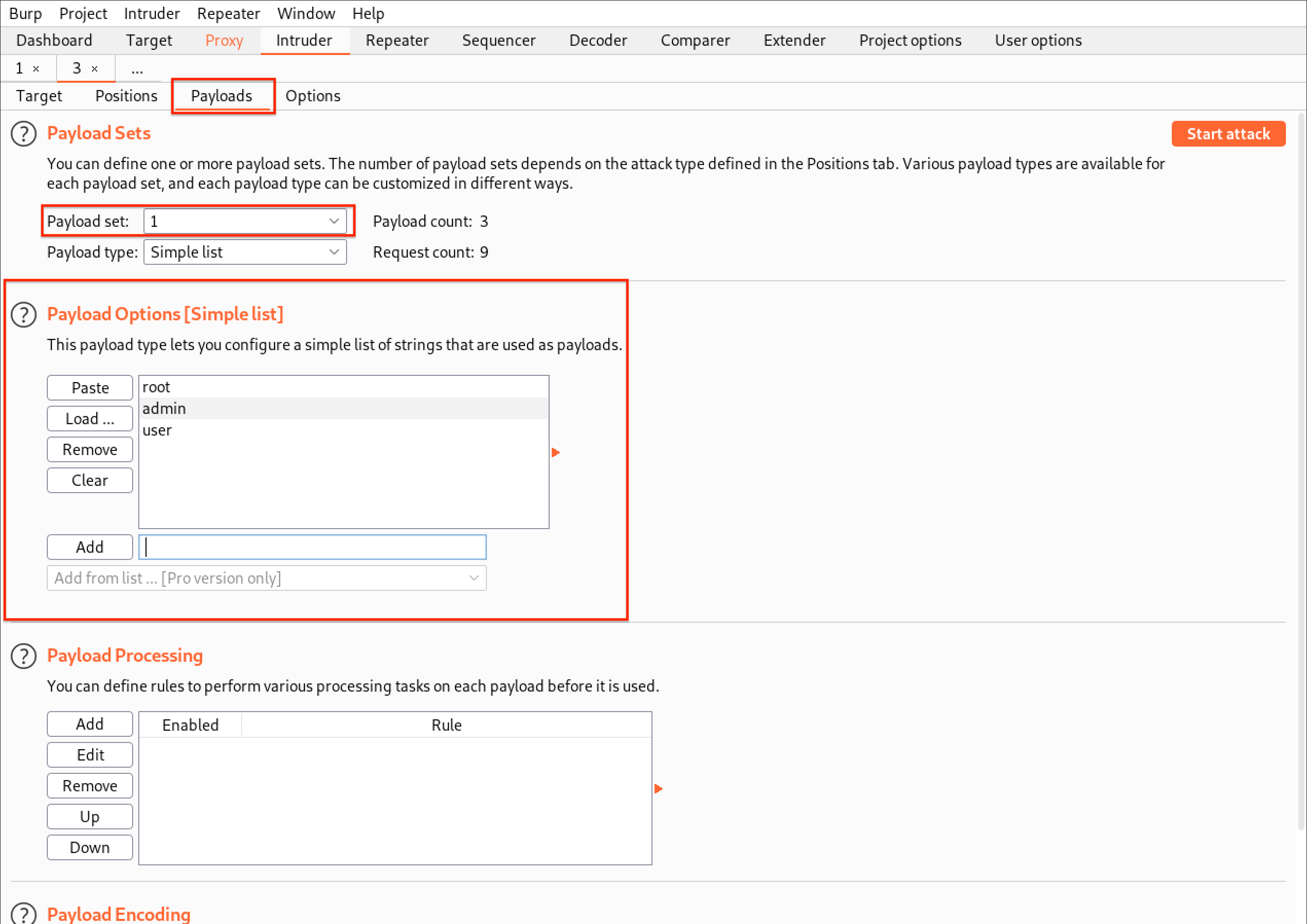

Start Attack and check different Length

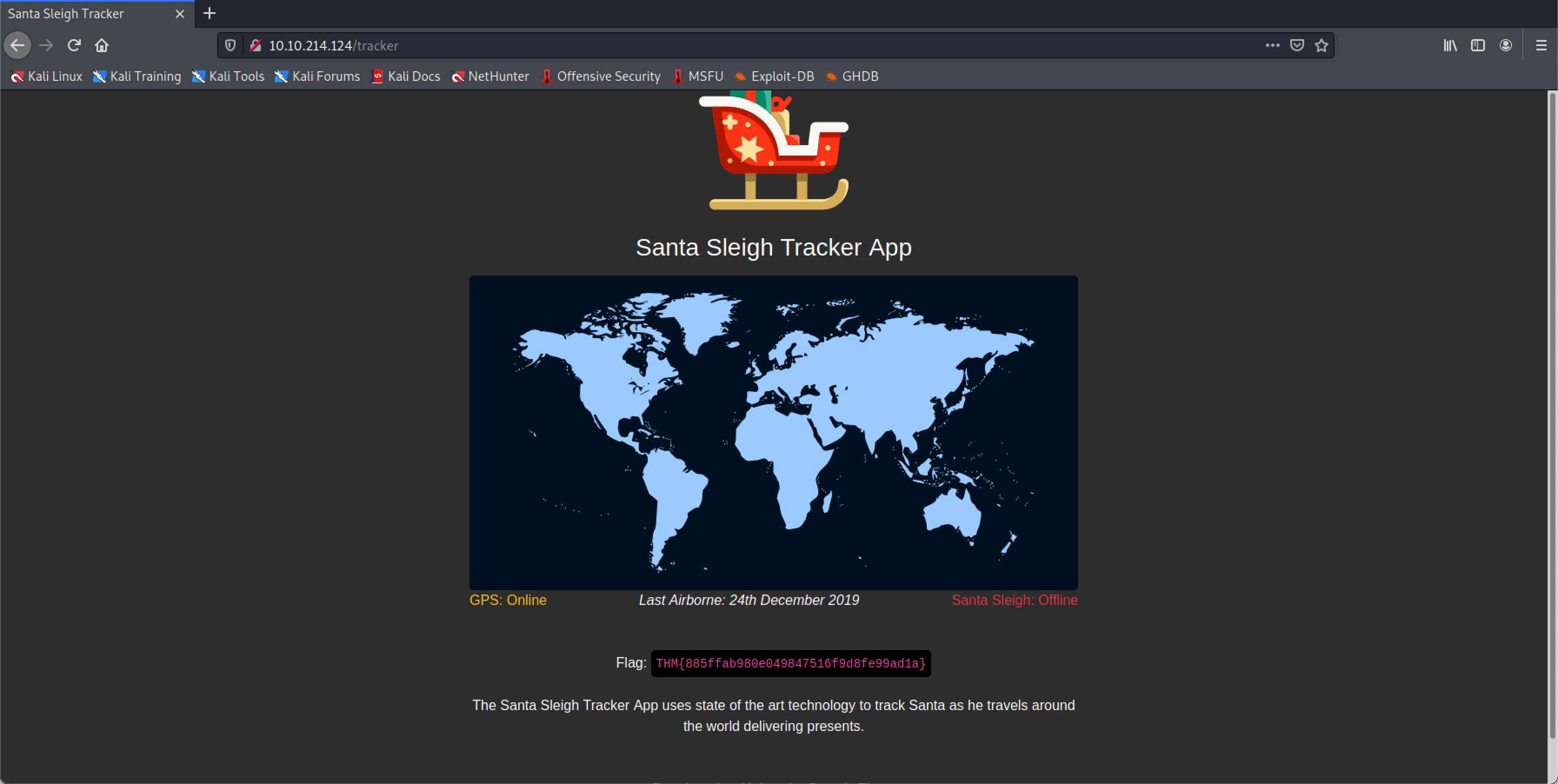
What is the flag?
THM{885ffab980e049847516f9d8fe99ad1a}
Login admin 12345
'Walkthrough > TryHackMe' 카테고리의 다른 글
| 25 Days of Cyber Security | Day 5 (0) | 2021.08.25 |
|---|---|
| 25 Days of Cyber Security | Day 4 (0) | 2021.04.27 |
| 25 Days of Cyber Security | Day 2 (0) | 2021.04.27 |
| 25 Days of Cyber Security | Day 1 (0) | 2021.04.16 |
| TryHackMe | Metasploit Write-up (0) | 2021.03.25 |




